A Hewlett-Packard’s white paper “HP ProtectTools: Authentication technologies and suitability to task“, 06/2005, does a very good job discussing the different security technologies available (Passwords, Trusted Platform Module, smartcard USB token, biometric fingerprints and virtual tokens) to authenticate a user to a computer or network. I was particularly drawn to the concluding chart (see below) where it compares the “Level of Security” vs. “Administration Complexity”.
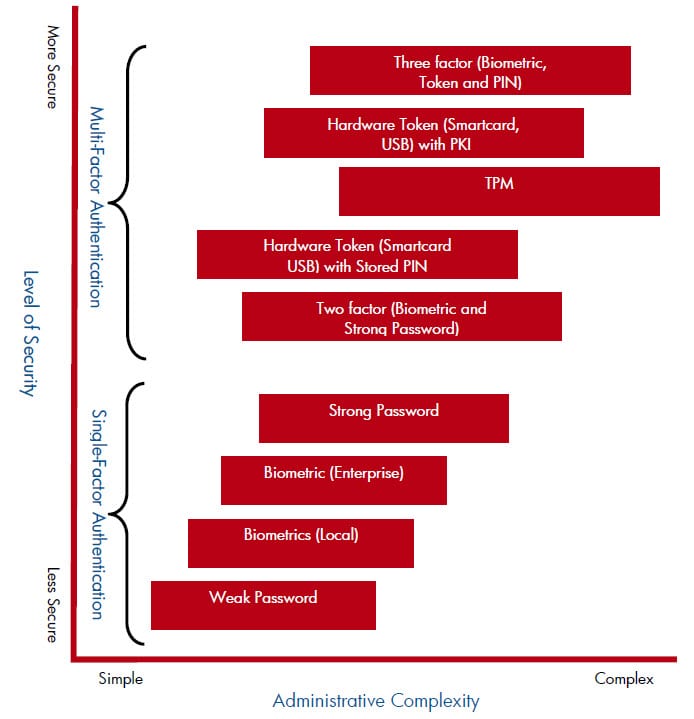
I often preach that it doesn’t matter how great a security technology is, if it’s too complex for users (or administrators) to use or manage then they will find ways to circumvent security for their own convenience. Biometrics is often promoted as being convenient and secure since every fingerprint is unique. But are these claims really true?
Many argue that the weaknesses to biometrics are its high false acceptance/rejections ratio, database management due to cuts, burns, etc., and the long wait time when comparing one-to-many. If the CEO cannot get into his/her computer using their fingerprint, IT will very soon get a very angry call. However, the one that I like best is that biometrics can never be kept secret – Everything you touch leaves biometric data behind.
Here are a few more observations about biometrics.
- Single factor authentication is so insecure that it needs to be disregarded on the spot.
- Strong passwords are more secure than biometrics.
- A hardware token like a smartcard is less expensive and more secure than a biometric+password.
Why these observations:
1) A card can be stolen, a password can be hacked, and a fingerprint template can be lifted. It is the combination of any two or all three that adds levels of security.
2) The combination of password length, character type and change frequency makes it virtually impossible to brute force attack. But fingerprints don’t change, so the only thing that can is the seed to generate the template. Since actual images are never stored the only way to update templates is with re-enrollment. Re-enrollment can be time consuming.
3) The cost of a biometric algorithm license, the reader and the maintenance for enrollment is much higher than most smartcards + password solution.
In conclusion:
Biometric is a way to authenticate users but it should never be used as the primary way. It is best to add for high security areas after a card and password has been presented. Finally, set up the biometrics to do a one-to-one comparison and not the one-to-many.



